mdex Support>RUT mdex OpenVPN Service
FAQ Important notes about using an mdex fixed.IP / public.IP via OpenVPN
When ordering the router with a mdex fixed.IP+ via OpenVPN or mdex public.IP via OpenVPN, the routers are already preconfigured ready for use. There are a few things to note regarding the router's OpenVPN functionality, especially when making subsequent changes to the router configuration:
From firmware version R_00.07.06.5
From firmware version R_00.07.05
From firmware version R_00.07.03
Up to firmware version R_00.06 (Legacy Firmware)
 openvpn for each newly created port forwarding rule to take effect.
openvpn for each newly created port forwarding rule to take effect.
 openvpn for each newly created port forwarding rule to take effect.
openvpn for each newly created port forwarding rule to take effect.
 openvpn for each newly created port forwarding rule to take effect.
openvpn for each newly created port forwarding rule to take effect.
2.2 DMZ Configuration (forwarding of all ports & protocols)
2.3 Port Forwarding
If the router is pre-configured with active DMZ Configuration (forwarding of all ports and protocols), this additional port forwarding rule "Router Remote Access" is activated. Remote access to the router via the respective mdex fixed.IP+/public via OpenVPN is then ensured, even if the wrong source zone wan has been set in the automatic rule tlt_allow_remote_http(s)_through_DMZ. When changing the router configuration, please note the following points:
If changes are made remotely, an additional port forwarding rule should first be created with the new LAN IP address and/or the changed HTTP/S port so that remote access is possible at any time with the old and new settings. As soon as the change has been made, the rule that is no longer required can be deleted.
If remote access is deactivated and is to be activated later, the following settings are required. 1:
From firmware version R_00.07.06.5
From firmware version R_00.07.05
From firmware version R_00.07.03
Up to firmware version R_00.06 (Legacy Firmware)
1. From firmware version R_00.07.06.5
1.1 Remote access to the router WebUI
The following forwarding rules are automatically created under Network -> Firewall -> Port Forwarding so that remote access to the router also works when DMZ (forwarding of all ports & protocols to a terminal device) is activated:| Port Forwarding Rule | |
|---|---|
| dmz_http: | HTTP remote access to the router |
| dmz_https: | HTTPS remote access to the router |
| dmz_ssh: | SSH remote access to the router |
| dmz_snmp: | SNMP remote access to the router |
| dmz_fw: | forwarding of all ports and protocols (DMZ) to this IP address (terminal device) |
Since version 7.06.5, the forwarding rules are automatically added with the required source zone, which is already set in the dmz_fw rule. This means that even with an mdex fixed.IP+/public via OpenVPN, it is no longer possible to lose remote access to the router by subsequently activating DMZ. Additional "workaround" scripts are no longer required since version 7.06.5.
1.2 DMZ and port forwarding
When using an mdex fixed.IP+ / public.IP via OpenVPN, the source zone must be changed manually by wan2. From firmware version R_00.07.05
2.1 Remote access to the router WebUI
The following forwarding rules are automatically created under Network -> Firewall -> Port Forwarding so that remote access to the router also works when DMZ (forwarding of all ports & protocols to a terminal device) is activated:| Port Forwarding Rule | |
|---|---|
| dmz_http: | HTTP remote access to the router |
| dmz_https: | HTTPS remote access to the router |
| dmz_ssh: | SSH remote access to the router |
| dmz_snmp: | SNMP remote access to the router |
| dmz_fw: | forwarding of all ports and protocols (DMZ) to this IP address (terminal device) |
When using an mdex fixed.IP+/public via OpenVPN with active DMZ, there are a few things to note:
1 A script is implemented under System -> Maintenance -> Custom Scripts for security purposes, which automatically adjusts the "source zone" of the rules dmz_http, dmz_https, dmz_ssh and dmz_snmp when the router is rebooted from wan
- For routers preconfigured by mdex for an mdex fixed.IP+/public via OpenVPN, the correct source zone "openvpn" is already set for all relevant rules.
- However, if "DMZ" is subsequently deactivated, all the above port forwarding rules are automatically deleted because they are no longer required.
- If "DMZ" is now reactivated, the above rules are automatically recreated, but all with the "wrong" source zone wan!
- In order for access via an mdex fixed.IP/public.IP via OpenVPN to work again, the source zones of these rules must be manually changed from wan
openvpn. The correct sequence must be followed so that remote access to the router is not lost:
- first change the source zone of the port forwarding rules dmz_http, dmz_https, dmz_ssh and dmz_snmp to wan
openvpn.
- the source zone of the last rule dmz_fw can then be changed from wan
openvpn without losing remote access. 1
openvpn if only the source zone of the rule dmz_fw has been changed to "openvpn". This means that remote access to the router is possible again at the latest after the next router reboot if the rule dmz_fw was accidentally changed to "openvpn" first. This script is included in all routers from firmware 7.05 that have been preconfigured as mdex fixed.IP+ / public.IP via OpenVPN.
System ->#!/bin/sh # mdex workaround: If the rule "dmz_fwd" is enabled and set to openvpn, the other fw rules "dmz_http", "dmz_https", "dmz_ssh" and "dmz_snmp" are also set to openvpn after the next router reboot. . /lib/functions.sh dmz_src="" src_updated=0 find_dmz_src() { local section="$1" local name="$(uci_get firewall "$section" "name")" if [ "$name" = "dmz_fw" ]; then dmz_src="$(uci_get firewall "$section" "src")" fi } update_dmz_fwds() { local section="$1" local name="$(uci_get firewall "$section" "name")" if [ "$name" = "dmz_http" ] || [ "$name" = "dmz_https" ] || [ "$name" = "dmz_snmp" ] || [ "$name" = "dmz_ssh" ]; then local src="$(uci_get firewall "$section" "src")" if [ "$src" != "$dmz_src" ]; then uci_set "firewall" "$section" "src" "$dmz_src" src_updated=1 fi fi } config_load "firewall" config_foreach find_dmz_src "redirect" [ -z "$dmz_src" ] && exit 0 config_foreach update_dmz_fwds "redirect" [ "$src_updated" -eq 0 ] && exit 0 uci_commit "firewall" /etc/init.d/firewall reload exit 0
2.2 DMZ and port forwarding
When using an mdex fixed.IP+ / public.IP via OpenVPN, the source zone must be changed manually by wan3. From firmware version R_00.07.03
3.1 Remote access to the router WebUI
To ensure that remote access also works reliably when using „DMZ“, a special script is implemented in all mdex preconfigured routers from firmware version R_00.07.03 under "Network -> Firewall -> Custom Rules".#!/bin/ash
###################################################################################################
# mdex workaround for router remote access, if dmz_fw is enabled:
## Check HTTP remote acccess:
HTTP_PORT="$(/sbin/uci get uhttpd.main.listen_http)"
HTTP_REMOTE_STATUS="$(/sbin/uci get uhttpd.main._httpWanAccess)"
if [ "${HTTP_REMOTE_STATUS}" == '1' ] ; then
iptables -t nat -A PREROUTING -i + -p tcp --dport ${HTTP_PORT} -j REDIRECT --to-port ${HTTP_PORT}
fi
## Check HTTPS remote acccess:
HTTPS_PORT="$(/sbin/uci get uhttpd.main.listen_https)"
HTTPS_REMOTE_STATUS="$(/sbin/uci get uhttpd.main._httpsWanAccess)"
if [ "${HTTPS_REMOTE_STATUS}" == '1' ] ; then
iptables -t nat -A PREROUTING -i + -p tcp --dport ${HTTPS_PORT} -j REDIRECT --to-port ${HTTPS_PORT}
fi
## Check SSH remote access
SSH_PORT="$(/sbin/uci get dropbear.@dropbear[0].Port)"
SSH_REMOTE_STATUS="$(/sbin/uci get dropbear.@dropbear[0]._sshWanAccess)"
if [ "${SSH_REMOTE_STATUS}" == '1' ] ; then
iptables -t nat -A PREROUTING -i + -p tcp --dport ${SSH_PORT} -j REDIRECT --to-port ${SSH_PORT}
fi
## Check SNMP remote access:
SNMP_PORT="$(/sbin/uci get snmpd.general.port)"
SNMP_REMOTE_STATUS="$(/sbin/uci get snmpd.general.remoteAccess)"
SNMP_PROTOCOL="$(/sbin/uci get snmpd.general.proto)"
if [ "${SNMP_REMOTE_STATUS}" == '1' ] ; then
iptables -t nat -A PREROUTING -i + -p ${SNMP_PROTOCOL} --dport ${SNMP_PORT} -j REDIRECT --to-port ${SNMP_PORT}
fi
###################################################################################################
Please note the following information:
- When using an mdex fixed.IP+ / public.IP via OpenVPN, the source zone of the rule Enable_HTTPS_WAN or Enable_HTTP_WAN must be set to openvpn under Network -> Firewall -> Traffic Rules!
- Subsequent changes to the router remote access, e.g. port changes, only take effect after the next router restart. If subsequent changes are made via remote access, there is a risk that remote access to the router will be lost until the next router restart!
- When updating the firmware from a "Legacy FW" to the current "Factory FW" (R_00.07.xx), the above-mentioned script is not automatically updated. If the "Keep all settings" option is activated, only the current configuration settings and existing rules according to Remote access to the router WebUI (legacy firmware) are applied.
3.2 DMZ and port forwarding
When using an mdex fixed.IP+ / public.IP via OpenVPN, the source zone must be changed manually by wan4. Up to firmware version R_00.06 (legacy firmware)
2.1. remote access to the router WebUI2.2 DMZ Configuration (forwarding of all ports & protocols)
2.3 Port Forwarding
4.1 Remote Access to the router WebUI
The routers are pre-configured with an mdex fixed.IP+/public.IP via OpenVPN with the correct source zone "From any host in vpn". For more information on remote access to the router's WebUI, see the FAQ Hints about router remote access.Due to this behaviour described above, the Teltonika routers are pre-configured with an mdex fixed.IP+ via OpenVPN or public.IP via OpenVPN since 11.3.2022 with an additional rule Router Remote Access from mdex, which is created under Network -> Firewall in the tab Port Forwarding:However, when using an mdex fixed.IP+ / public.IP via OpenVPN and DMZ Configuration, there are other things to be aware of:.
- The ports and protocols that are forwarded when DMZ Configuration is active (forwarding all ports and protocols), the additional (automatic) port forwarding rule tlt_allow_remote_https_through_DMZ for remote access to the router WebUI is preconfigured with the correct source zone "From any host in vpn".
- However, the soruce zone of this rule tlt_allow_remote_http(s)_through_DMZ will be changed by the router to wan if configuration adjustments were subsequently made to remote access or port forwarding and the firewall or updated by clicking Save, e.g.:
- An additional port forwarding rule is added although DMZ Configuration is still activated.
- DMZ Configuration" is subsequently deactivated and then reactivated.
- DMZ Configuration" was deactivated at the time of delivery and is now subsequently activated.
- The router remote access was deactivated and is now subsequently activated.
- Remote access to the router's web interface via the mdex fixed.IP+/public.IP via OpenVPN is now no longer possible!
In order for remote access to work again, the rule tlt_allow_remote_http(s)_through_DMZ must be manually switched back to Source "From any host in vpn" under Network -> Firewall in the Port Forwarding tab!
| Port Forwarding Rule | |
|---|---|
| Name: | Router Remote Access |
| Protocol: | TCP |
| Source zone: | vpn |
| External Port: | Port for external remote access to the router (e.g. 4444) |
| Internal zone: | lan |
| Internal IP address: | router LAN IP address (e.g. 192.168.1.1) |
| Internal port: | HTTP/S port of the router (e.g. 4444) |
4.1.1 Changing the Router LAN IP Address or HTTP(S) Port
If the LAN IP address or the HTTP/S port of the router is subsequently changed, this Router Remote Access rule must also be adjusted manually. Otherwise, remote access may no longer be possible if, for example, "DMZ Configuration" is also used.If changes are made remotely, an additional port forwarding rule should first be created with the new LAN IP address and/or the changed HTTP/S port so that remote access is possible at any time with the old and new settings. As soon as the change has been made, the rule that is no longer required can be deleted.
4.1.2 Disable Remote Access
If remote access to the WebUI of the router is no longer desired, the router remote settings and the additional rule Router Remote Access must be deactivated. 1:- deactivate Remote Settings under System -> Administration in the tab Access Control:
WebUI Enable remote HTTP access: 
Disable HTTP remote access to the WebUI of the router Enable remote HTTPS access: 
Disable HTTPS remote access to the router's WebUI
1. under Network -> Firewall in the tab Port Forwarding disable the rule Router Remote Access:
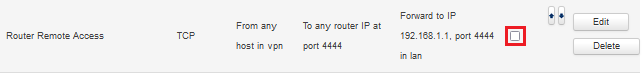
4.1.3 Enable Remote Access
We generally recommend setting up the HTTPS port 4444 for remote access to the router WebUI.If remote access is deactivated and is to be activated later, the following settings are required. 1:
- activate remote settings under System -> Administration in the tab Access Control:
WebUI Enable remote HTTPS access: 
Enable HTTPS remote access to the WebUI of the router Port: 4444 HTTPS port of the router
- activate the rule Router Remote Access under Network -> Firewall in the tab Port Forwarding (and adjust with Edit if necessary).
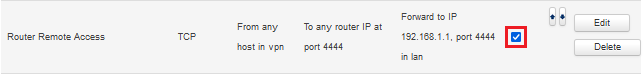
- If the router LAN IP address and/or the HTTPS port have been changed in the meantime, this rule must be adjusted accordingly with Edit.
- If this rule is missing, it must be added manually with New Port Forward Rule:
New Port Forwarding Rule Name: Router Remote Access Protocol: TCP Source zone: vpn External Port: Port for external remote access to the router (e.g. 4444) Internal zone: lan Internal IP address: router LAN IP address (e.g. 192.168.1.1) Internal port: HTTP/S port of the router (e.g. 4444)
4.2 DMZ Configuration (Forwarding of all Ports & Protocols)
If the router is preconfigured with a fixed.IP+ / public.IP via OpenVPN, the correct source zone vpn is already preset under Network -> Firewall at DMZ Configuration. All incoming ports and protocols to the fixed.IP/public.IP are forwarded to the set IP address DMZ host IP address. If remote access to the router's WebUI is also desired, please be sure to observe the notes under 1. Remote Access to the Router WebUI. The source zone for DMZ Configuration cannot be changed via the WebUI, but would have to be adjusted via SSH if necessary (e.g. for manual reconfiguration):| Source zone | SSH commands | Info |
|---|---|---|
| vpn: | /sbin/uci set firewall.DMZ.src='vpn' /sbin/uci commit firewall |
access via fixed.IP/ public.IP via OpenVPN |
| wan: | /sbin/uci set firewall.DMZ.src='wan' /sbin/uci commit firewall |
Access via IP address of SIM card |
4.3 Port Forwarding
If instead of forwarding all ports and protocols to a terminal device (DMZ Configuration), an individual port forwarding of only the required ports is to be set up, follow the steps below. 1:- under Network -> Firewall, deactivate the DMZ Configuration option so that all ports not covered in the port forwarding table are no longer forwarded to this terminal device.
- Under Network -> Firewall in the tab Port Forwarding add a new port forwarding rule with Add.
-
 For each port forwarding rule added, now click on Edit and change the Source zone from wan: wan to vpn: openvpn !:
For each port forwarding rule added, now click on Edit and change the Source zone from wan: wan to vpn: openvpn !:
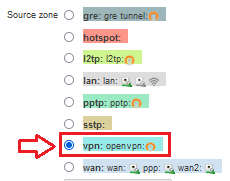
Only then is the terminal device accessible via the mdex fixed.IP+ / public.IP via OpenVPN.
- Häufig gestellte Fragen
- mdexmobile.LAN Paket
- mdexRouter RUT104
- mdexRouter MX510
- mdexpublic.IP
- mdexfixed.IP+
- mdexLeitstellentunnel
- SIM-Karten
- Fragen zur Sicherheit
- mdex Kontakt
-
 support@mdex.de
support@mdex.de
-
 +49 4109 555 333
+49 4109 555 333


